Why is Routing Security Adoption Moving So Slowly?
In short
- Networks adopting routing security best practices can reduce the risk of having their customer's traffic hijacked.
- Geography, network size, business category, and the complexity of the address space impact routing security adoption levels.
- New findings can inform policymakers' efforts to understand challenges and advocate for greater routing security adoption.
Routing security is not a new problem. For decades, we have known that the de facto protocol designed to enable inter-domain routing—the Border Gateway Protocol (BGP)—has a critical vulnerability: it lacks a built-in mechanism for validating the information that networks share and uses to select global routes for data traffic.
This means that when networks decide where to send online traffic, they often have no way of verifying that they are sending it to a network that can deliver that traffic to its intended address. As a result, online traffic often gets routed to the wrong networks, whether accidentally or maliciously, a type of problem sometimes called BGP hijacking.
Because BGP hijacking has existed for a long time, researchers and technologists have devised various ways to prevent it. One of the most used solutions is a framework called Resource Public Key Infrastructure, or RPKI, which was standardized by the Internet Engineering Task Force in 2012.
The RPKI framework enables networks to issue cryptographic records that other networks can use to validate data in BGP, effectively ensuring that online traffic cannot be hijacked. However, to fully benefit from RPKI protection, networks need to issue RPKI records for the entire IP address space they use.
See how much of your country's IP address space has issued RPKI records.
Frustratingly, even though RPKI has been around for more than a decade, adoption has been slow. Today, in 2024, only about half of the IP addresses advertised in BGP are covered by RPKI records.
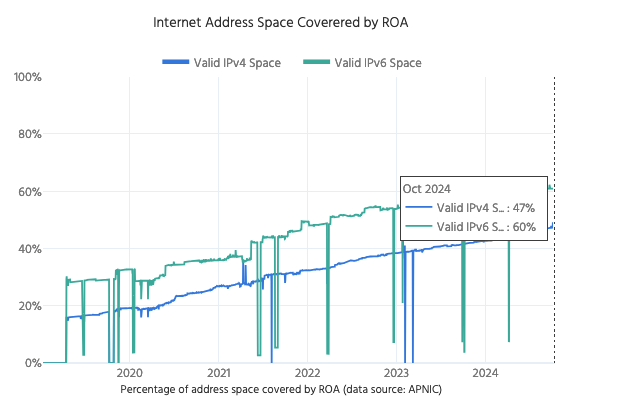
Our research seeks to understand why RPKI adoption has been so slow, given that the security risks it addresses are well-known and which types of organizations are lagging in adopting RPKI. We hope these findings can inform policymakers' efforts to boost RPKI adoption and better secure BGP. This is particularly relevant when the US government is making a renewed push to address routing security.
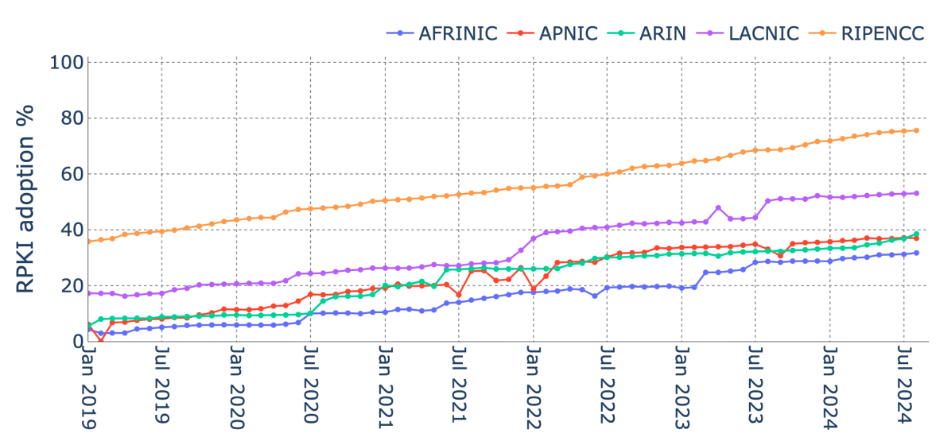
Region and Network Size Play Big Role in RPKI Adoption
In our analysis, we found four key characteristics that impact organizations' RPKI adoption levels: geography, network size, business category, and the complexity of the address space.
We believe the geographic heterogeneity results from the fact that the Regional Internet Registries (RIRs) have independently implemented the process and requirements for issuing RPKI records. As a result, the levels of adoption vary across the geographical zone each RIR covers.
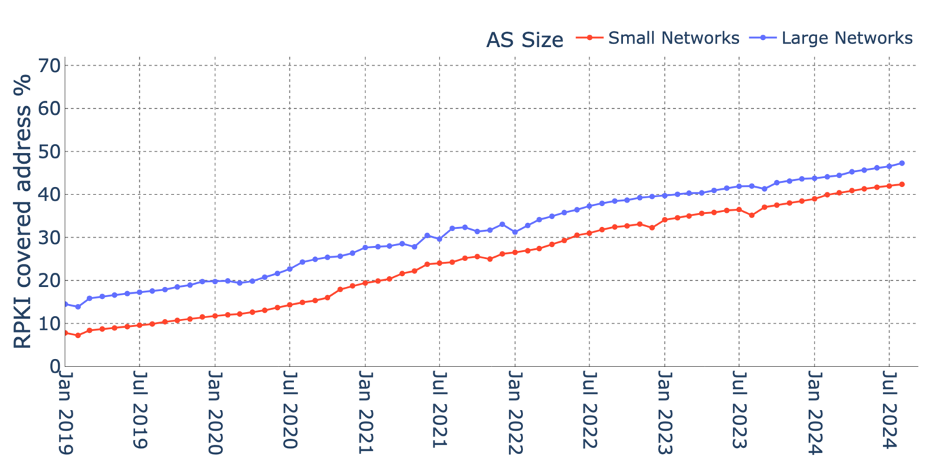
Additionally, the size of a network is an important factor because RPKI requires additional management and operation, and smaller networks find it more challenging to add that to their regular operations.
Furthermore, networks from organizations unrelated to Internet services, such as educational and government networks, have even less awareness of RPKI and fewer incentives to adopt it than organizations with closer ties to online services.
Finally, even for large networks, all IP addresses differ in terms of the effort required to issue RPKI records. Legal and operational challenges linked to the delegation and sub-delegation of address space may make RPKI adoption harder for some portions of their address space.
Read our paper for more details about the study and the results.
We plan to use these results as a starting point for a broader study of the barriers these lagging organizations face in adopting RPKI and, ultimately, to propose potential policy solutions to help address these challenges in the future.
Contributors: Cecilia Testart, Deepak Gouda, and Romain Fontugne
Josephine Wolff is an Associate Professor of Cybersecurity Policy at The Fletcher School at Tufts University.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of the Internet Society.

