Why DNS Resolvers Are the Next Internet Frontline
In short
- Governments increasingly turn to DNS-level blocking interventions because they're easy to implement.
- Study show a drop in usage of public DNS services is making DNS blocking efforts easier.
- Browser-based security, user-level content filtering, and greater transparency are alternate ways to implement censorship without erasing connections.
Domain Name System (DNS) resolvers are the quiet backbone of our daily Internet life. Their steady performance keeps us connected, resolving domain names, delivering websites, and enabling every ping and click. Their role in infrastructure makes them a battleground for Internet freedom.
Whether authoritarian or democratic, governments increasingly turn to DNS resolvers as enforcement tools. Blocking orders—often legally vague—are routinely sent to Internet Service Providers (ISPs), who default to DNS-level interventions because they're easy to implement.
But easy doesn't mean benign.
As Douglas Fischer, a Brazilian network engineer, warned, users lose trust when ISPs block domains without explanation. That mistrust can push them toward public DNS resolvers, sometimes more trusted but not always more transparent.
Digital Medusa's latest report, produced with data contributions from Sebastian Castro (.IE), researches the DNS resolvers landscape—tracing consolidation patterns, censorship, and governance patterns. Here's a peek at what we found and why it matters.
Usage of Public DNS Resolvers Is Shrinking (But Not Uniformly)
Based on APNIC data, DNS resolver usage has halved since 2022. This might sound like decentralization is winning, but that's only part of the picture.
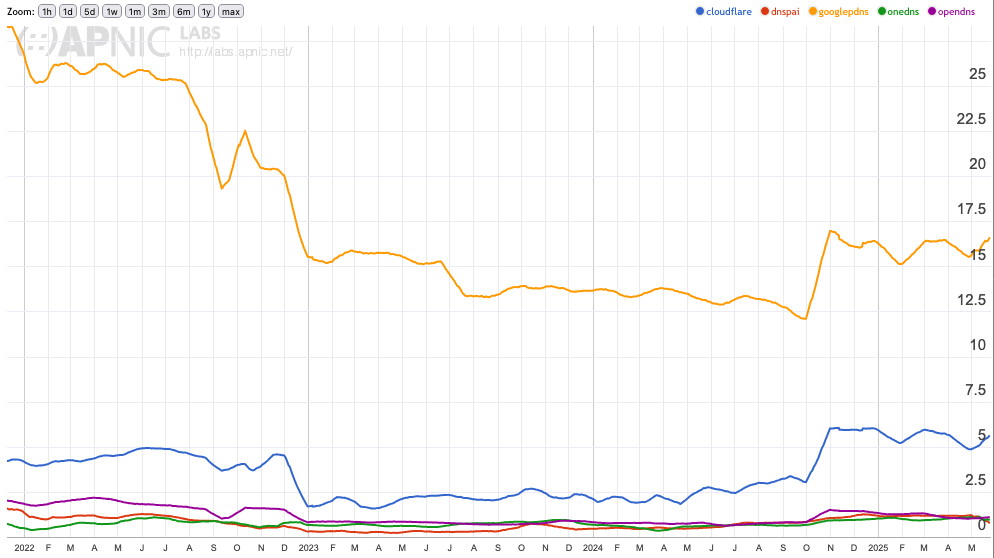
Some users still rely on a few globally dominant public DNS resolvers. The shrinkage isn't evenly distributed across countries or regions. As the pool of resolvers shrinks, the influence of the remaining ones grows. This concentration makes it easier for governments and powerful actors to pressure or coerce them, often in ways that diminish user rights and fragment the global Internet.
Open-Source Software Is Necessary—but Not Sufficient
Open-source DNS resolvers are a transparency win and can contribute to decentralization, but sustainability and scale remain tough.
Many operators support open-source tools, but large-scale, resilient deployment needs more than just code. We also need strong community governance models to make these tools viable alternatives to centralized, corporate-run services.
In short, open code without open stewardship isn't enough. If we want decentralization to be real, we must build infrastructure and institutions.
Further, we must equip the Internet's defenders with counter-narratives and evidence, showing governments what DNS blocking does to access and trust. Efforts like the RIPE NCC Task Force on Best Practices for DNS Resolvers are laying the essential groundwork, offering transparency, accountability, and trust preservation guidelines.
Freedom Relies on Public DNS—Especially Where It's Most Fragile
Our research shows that in places like Central Asia and West Africa, where press freedom and Internet openness are limited, users often use public DNS resolvers to bypass local censorship.
But, this workaround is only as strong as the resolvers' policies and independence. If governments can pressure a handful of providers, they can cut off these vital escape routes.
This brings us full circle: the resilience and diversity of DNS resolvers aren't just technical issues; they're freedom issues.
Further research is needed to understand how public DNS resolvers are used during political events and uprisings. We have provided some recommendations on how we can potentially measure it.
Rendezvous Disrupted: Rethinking DNS Blocking
Imagine walking down a street looking for a lifeline.
You've heard of a place—a center, a shelter, a gathering point. Maybe it's a legal aid clinic, an LGBTQI support group, or a survivor resource hub. You know the name. You've typed it into your browser. But when you try to visit, nothing happens. No message. No explanation. Just an invisible wall.
There's no sign telling you where it went, no door to knock on, no hint that it ever existed, and no one to report it to. Or imagine you are simply trying to access a Google Drive link, but you can't because it's blocked.
DNS-level blocking doesn't just restrict access to content—it erases digital pathways to services and spaces that people rely on for daily living and sometimes for services people rely on for safety, solidarity, and survival. It disrupts what Internet engineers call the "rendezvous"—the point at which two endpoints, like a browser and a server, come together and make a connection.
So, what would a "No Rendezvous Disrupted" approach look like?
- Browser-Based Security: Modern browsers already know how to protect users. They can detect phishing sites, warn about expired certificates, and flag known malware domains. Instead of breaking DNS resolution, we can use browsers to display meaningful, context-aware warnings, allowing users to understand the risk rather than hiding the content altogether.
- User-Level Content Filtering: Instead of top-down censorship, empower individuals. Tools at the home network or device level allow users, parents, or schools to set their own content preferences. This approach is decentralized, flexible, and respects agency while still providing safety.
- Transparency and Notice: If something must be blocked, tell the user why. Redirect to a notice page. Include information about the legal basis, the issuing authority, and an appeal mechanism.
We Need More Rendezvous
The DNS is one of the few infrastructural points where openness and resilience can still be reclaimed. But doing so means breaking the habit of centralization, resisting DNS-level censorship, and investing in open, sustainable, and community-governed alternatives.
If we don't respond with better systems, more transparency, and smarter policies, we may become increasingly disconnected from the open web we rely on.
Read the full report
Farzaneh Badiei is a recovering academic and founded Digital Medusa to petrify the enemies of a global, interoperable Internet.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of the Internet Society.
Photo by Annie Spratt on Unsplash

