The Mongolian parliament is reviewing a controversial law that gives the minister of internal affairs the power to shut down access to the Internet.
The law, which was hastily passed by the parliament in January and then quickly vetoed by the president, would remove the ability of 3.3 million people to communicate, learn, and earn a living, and in the process damage the country’s economy.
The Pulse team has recently seen an increase in the number of countries implementing such legislation, representing a negative trend towards an open and less resilient Internet.
Built-in Control Through National Internet Gateways
Several countries, including Azerbaijan, Iran, and Lebanon, have built their Internet in a way that provides the government with complete control over all the traffic flowing in and out of the country through national Internet gateways.
In these countries, all Internet Service Providers (ISPs) must buy access directly from a single entity connected to the government, meaning all traffic transits through the government’s network, where it can be controlled and, potentially, blocked.
This configuration is attractive to these governments as it allows for increased security measures, easier surveillance, and a higher potential for Internet limitations and shutdowns.
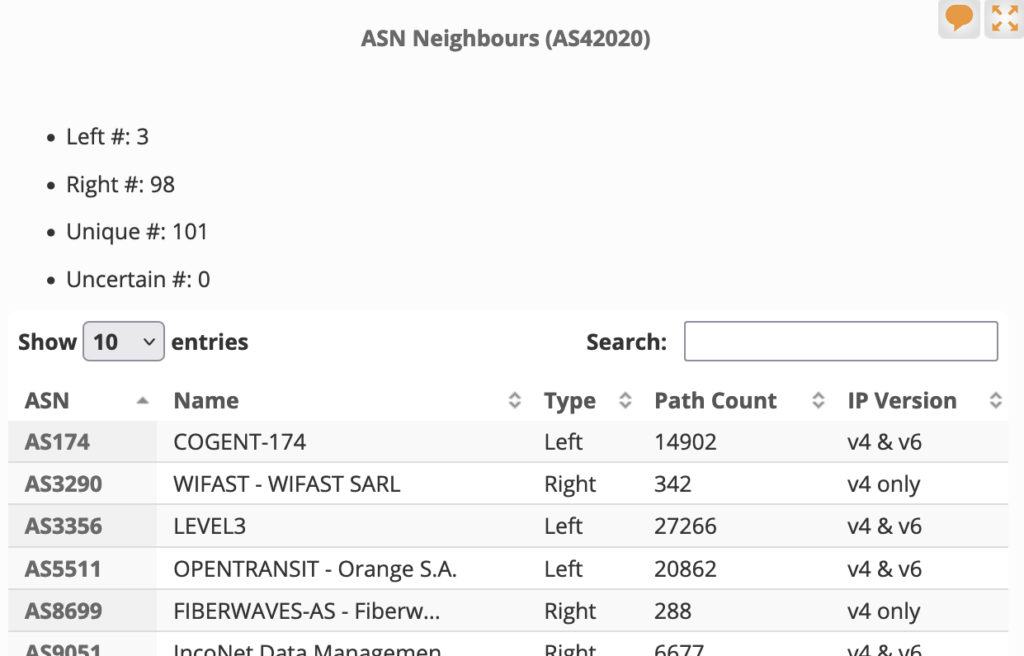
If we look at Lebanon’s configuration using RIPEstat (Figure 1), the Lebanese government’s network operator Ogero (AS42020), has 101 unique neighbors, or relationships with other Autonomous Systems (ASes). Of these,
- Three are classified as ‘left’ type, meaning they are transit operators (Cogent, Level3, and Opentransit), which allow Ogero to reach the global Internet.
- 98 are classified as ‘right’ type, meaning they are downstream customers, that is all networks in Lebanon.
Aside from the privacy concerns, these national gateway configurations reduce market share (increasing market concentration) and create a single point of failure that jeopardizes the resilience of the country’s connectivity to the global Internet.
While Iran has one of the most controlled domestic Internets in the world, the government enforces the use of Resource Public Key Infrastructure (RPKI) for all its customers.
Almost every network in Iran is covered by a Route Origin Authorization (ROA), which helps to avoid hijacks and misconfigurations having a detrimental impact on the country’s Internet.
Learn more about routing security and how the Internet Society is supporting a global, community-led initiative to implement best practices to reduce the most common routing threats.
While a national gateway providing a single-entry point for the Internet provides for tight control of network topology, encrypted traffic would still transit through it without any problem. This is where Deep Packet Inspection (DPI) comes into play.
Using Deep Packet Inspection (DPI) to Inspect Encrypted Traffic
To understand how this is possible, we need to consider that a large percentage of Internet traffic now uses TLS or QUIC as transport vectors. While both encrypt packets, the notable difference between the two is QUIC encrypts not only the details of the communication but most of the connection metadata from observers, such as the Server Name Identifier (SNI). The SNI indicates which server a user is trying to contact—such as www.isoc.org—making it easy for an external actor intercepting the communication to understand where this is directed.
In the case of QUIC, intercepting the SNI is more complicated, so the chances that an external actor intercepts it and uses that info to either block the connection or redirect it is minimal.
This is why we have recently observed the following phenomenon in Russia and Iran (Figures 2 and 3).
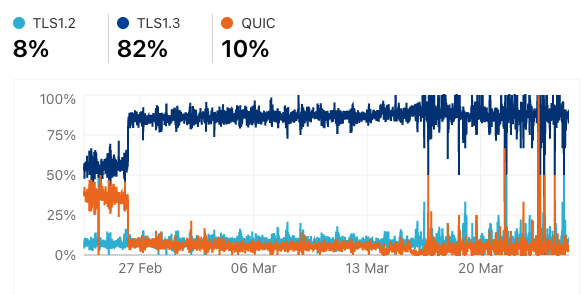
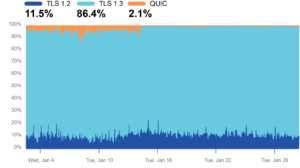
In both examples, we can see that the use of QUIC dropped drastically at one point in time. We believe this is due to the introduction of ‘middle boxes’ that inspect traffic but can’t handle QUIC. This could be considered preparation to perform more in-depth inspection and user blocking.
Building Control Through Regulation
Mongolia is the country in the news today, but other countries such as Azerbaijan and Kazakhstan have also shown they are preparing to exert more government control over the Internet:
- On 27 September 2020, the government of Azerbaijan announced it would restrict access to the Internet amid growing tensions between Armenia and Azerbaijan over competing claims to the Nagorno-Karabakh border region.
- Kazakhstan tried to introduce a national certificate in 2019, which would have allowed the government to ‘read’ any encrypted communication.
There have also been reports of ISPs in Russia and Iran needing to host provider edge black boxes that are controlled by their respective governments. The provider edge boxes not only allow for surveillance but can be used to cut external connectivity.
The latest move by the Mongolian parliament, although averted by the presidential veto, shows that the urge for controlling access to the Internet is not cooling down, but rather moving around between tactics and tools.
At the Internet Society—enablers of an open, globally-connected, secure, and trustworthy Internet—the Pulse team is monitoring these worrying developments.


