Internet Security - Are You Up To Date?
Many popular Internet applications like e-mail and web browsers use Transport Layer Security (TLS) to secure traffic against eavesdropping and against data being tampered with while in transit between clients and servers. Over time, flaws in early versions of TLS have been identified leading to substantial improvements to the protocol.
The documents defining version 1.0 and version 1.1 of the Transport Layer Security standard have now been assigned the status of Historic by the Internet Engineering Steering Group (IESG). A new Best Current Practice has been published by the Internet Engineering Task Force (IETF) to formally deprecate TLS 1.0 and TLS 1.1. As that document explains,
These versions lack support for current and recommended cryptographic algorithms and mechanisms, and various government and industry profiles of applications using TLS now mandate avoiding these old TLS versions. TLS version 1.2 became the recommended version for IETF protocols in 2008 (subsequently being obsoleted by TLS version 1.3 in 2018), providing sufficient time to transition away from older versions. Removing support for older versions from implementations reduces the attack surface, reduces opportunity for misconfiguration, and streamlines library and product maintenance.
RFC 8996 Deprecating TLS1.0 and TLS1.1
Related recommendations from national security agencies have also recently been published (h/t Bulletproof TLS Newsletter):
- The NSA published documentation discouraging the use of old TLS versions 1.0 and 1.1 and published accompanying tools and configuration examples.
- The dutch National Cyber Security Centre (NCSC) published a document with security guidelines for TLS, notably recommending the use of TLS 1.3. The security of TLS 1.2 was downgraded from “Good” to “Sufficient” by the NCSC.
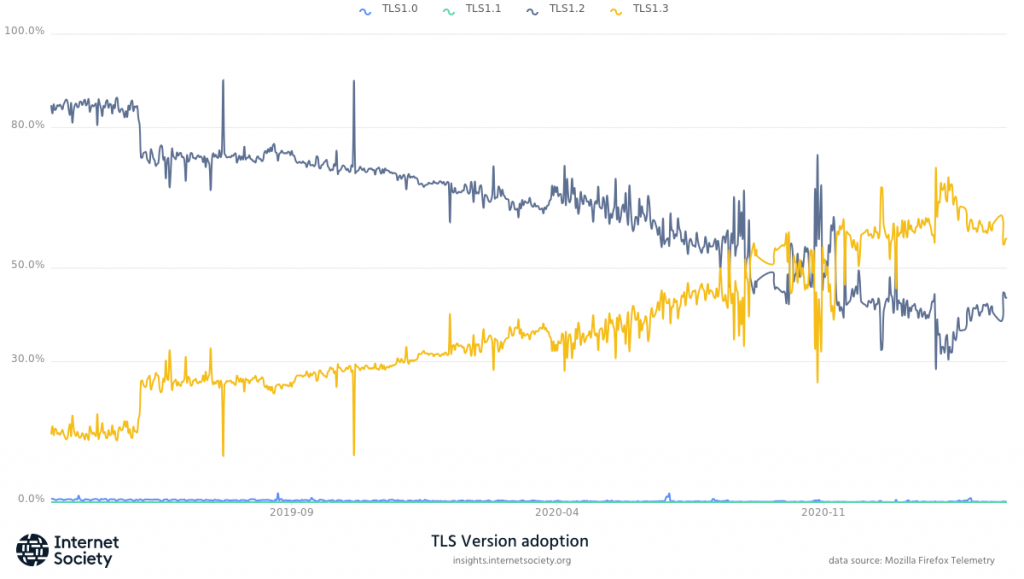
The latest version of TLS, TLS 1.3, provides enhanced security and fewer ways for attackers to find new flaws. TLS 1.3 has also been shown to improve performance, with secure connections taking less time to be established. This helps to demonstrate that optimizations can be made without compromising on security. Improving the security of Internet applications of all kinds is imperative for a healthy and growing Internet. Follow the adoption of TLS1.3 on our Pulse Enabling Technologies page.
Photo by Parrish Freeman on Unsplash

