Exploring the Internet's Router Vendor Diversity
Routers are critical components of the Internet’s physical infrastructure, connecting networks and directing traffic. Despite this, little is known about their composition, specifically their make: Operators rarely share information on what router vendors they use, and remotely identifying router vendors is challenging due to their strict security posture and indistinguishability (due to code sharing across vendors).
Gaining such insight is essential to understanding the potential correlated failures of network hardware, the diversity of network infrastructure, and the resilience of the Internet.
Recently, my colleagues and I at TU Berlin, Max Planck Institute for Informatics, the Center for Measurement and Analysis of Network Data, and Delft University of Technology developed a technique to remotely identify (fingerprint) router vendors.
Using this technique, we found that Cisco is the dominant maker of routers, with about 49% of the identified router interfaces, followed by Juniper (29%) and Huawei (12%).
Lightweight Fingerprinting
Our technique uses a set of features to generate a signature for the target router and subsequently compares this signature to an existing set of known signatures associated with a specific vendor. We limit the features to data obtained mainly from the IP layer. Our goal is to minimize the measurement overhead and avoid disrupting network operation (that is, due to malformed packets).
This led us to rely on nine simple probes, three per protocol: TCP, UDP, and ICMP.
Router Vendors on a Path
One of the applications we envision for this work is making informed routing decisions based on vendors on a path. Such routing decisions can potentially have security and policy implications. For example, a security vulnerability may be specific to a particular vendor and implementation and thus will disproportionately impact specific networks and paths if exploited.
To explore the feasibility of this idea, we applied our technique to a single-day snapshot of the RIPE Atlas traceroute dataset. This dataset contains more than 7.6M traceroute measurements and around 327k responsive intermediate hops.
From this, we identified the vendor for 56% of hops. We could not get a signature for the remaining targets as they either responded to only one probe type or did not respond.
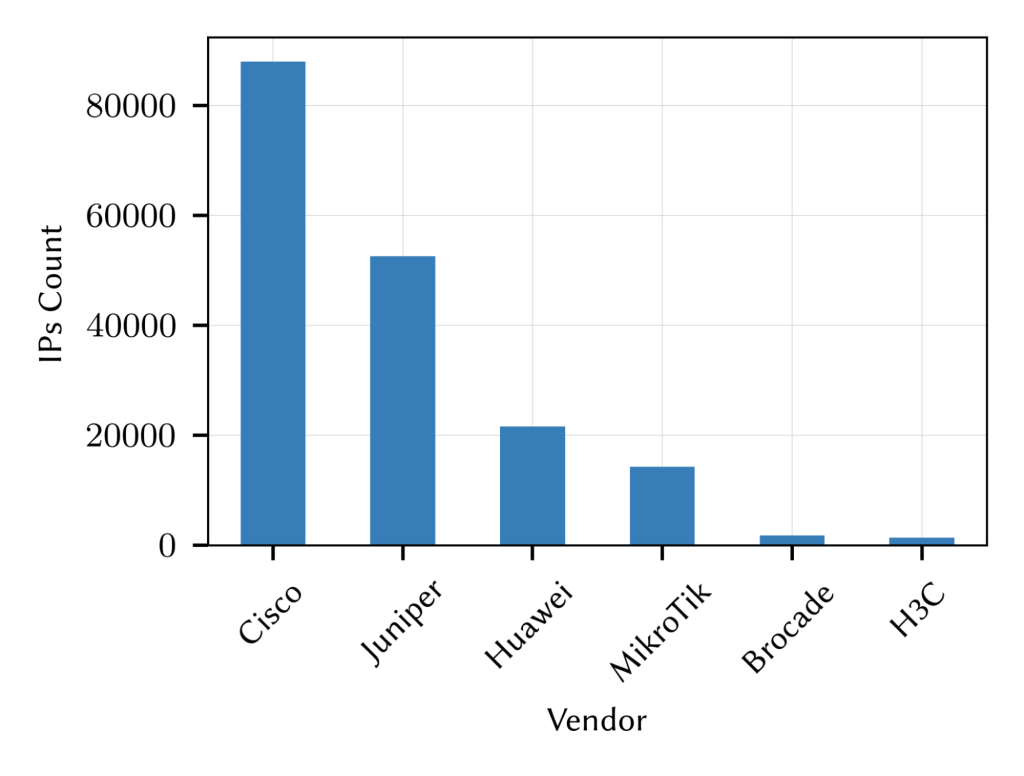
In Figure 1, we report the top six vendors observed in this dataset. Notably, Cisco is dominant, with about 49% of the identified router interfaces, followed by 29% Juniper, 12% Huawei, and 7% Mikrotik. The remaining 3% is split between nine different vendors.
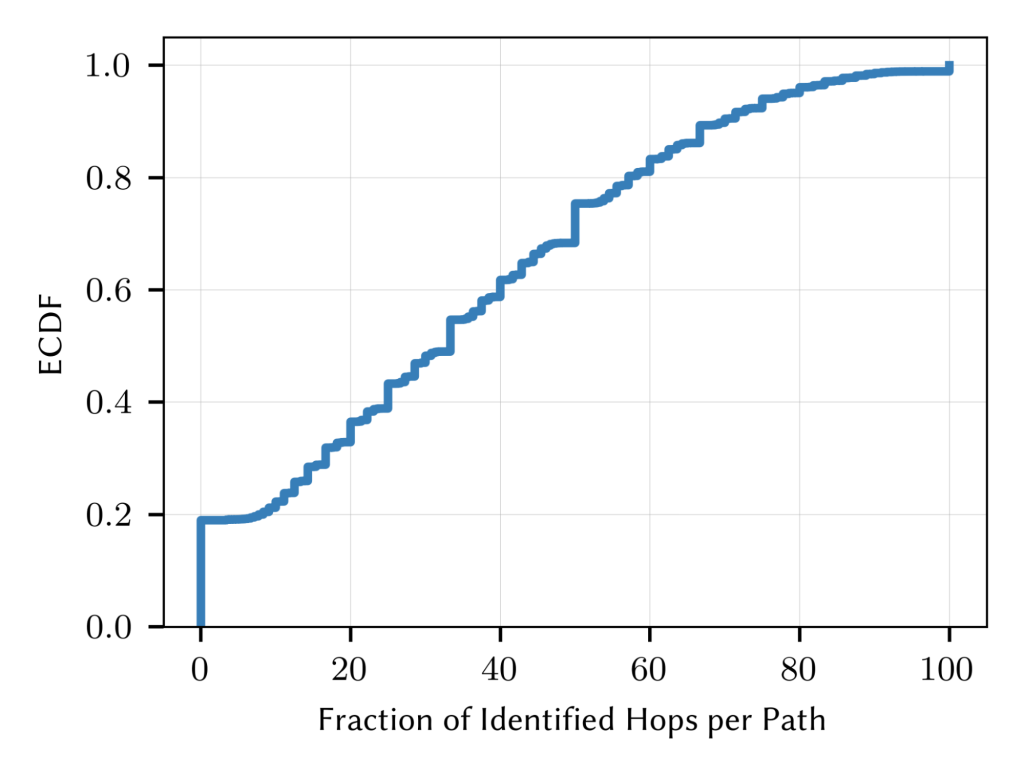
Further, as per Figure 2, ., we see that for 20% of traces, we did not identify any hop. However, for about 40%, we identified between 40 to 90% of hops. This indicates that although we can rarely fingerprint a full packet path, for around 35% of traces, we can fingerprint at least half of the hops of these traces.
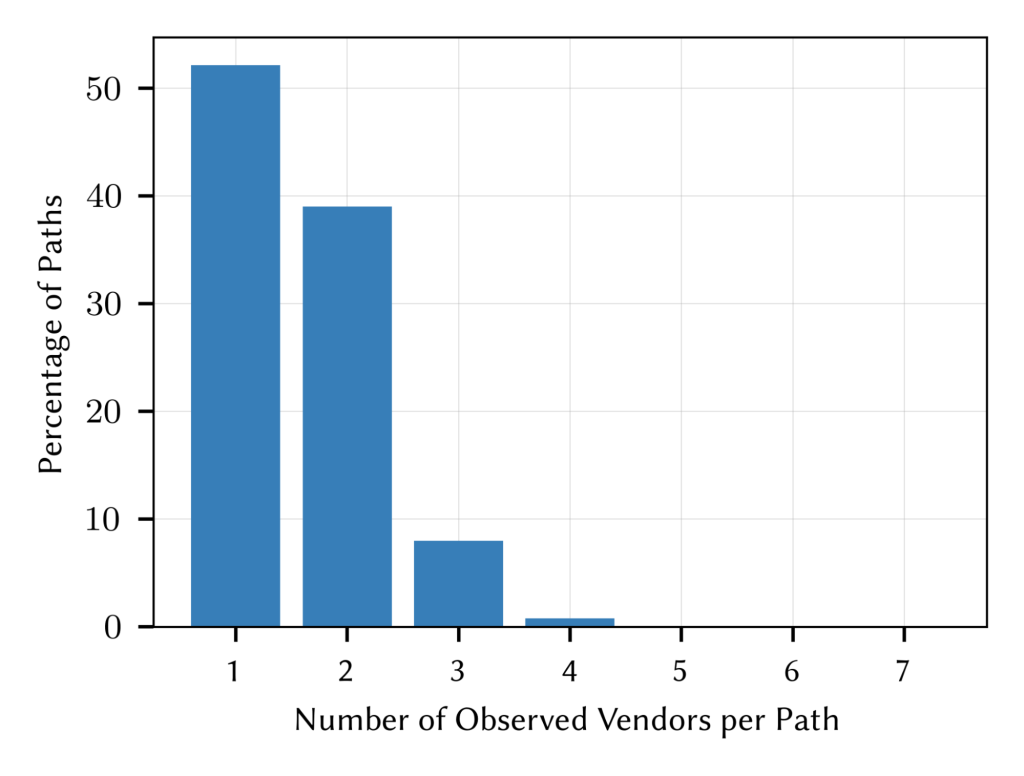
Here, we looked into how many vendors and vendor combinations are observable. As per Figure 3, we showed that around 90% of paths comprised of routers developed by one or two vendors, whereas three or more vendors are visible in 10% of cases.
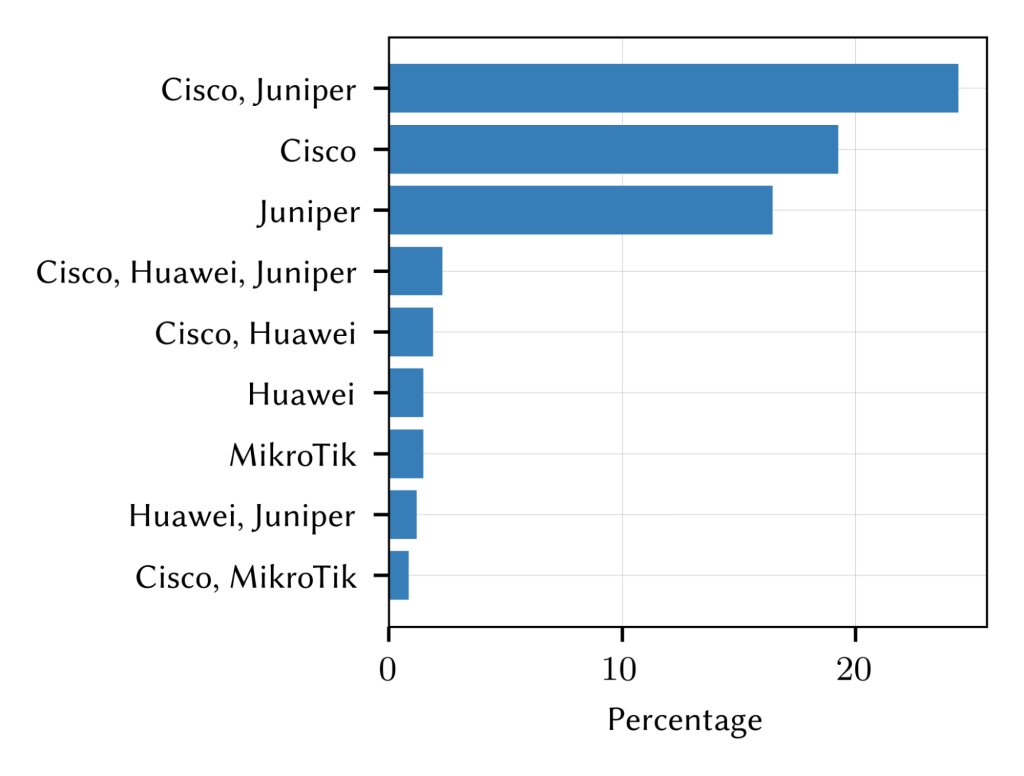
As for vendor combinations on a path, we observed more than 160 unique combinations. However, only nine combinations cover 70% of all traces (Figure 4).
Challenges and Future Work
Although the ground truth data we use is relatively large, we recognize it may not necessarily represent all routers on the Internet.
Additionally, our work focuses on IPv4 addresses and provides no insight into the IPv6 world.
In future work, we plan to examine the consistency of the signatures and the potential of fingerprinting routers beyond the vendor level. We also plan to work on fingerprinting routers over IPv6.
To learn more about this work and access our data, read our ACM IMC 2023 paper, Illuminating Router Vendor Diversity Within Providers and Along Network Paths, and visit our GitHub page.
Taha Albakour is a PhD student at TU Berlin focusing on Internet measurement and security.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of the Internet Society.

