App Servers not ISPs are Blocking App Usage in India
In June 2020, India officially banned 59 Chinese apps for the first time, stating that these apps threatened the privacy and data security of Indian users. By November 2020, the number of banned apps increased to 220.
The banned apps were not only removed from Google and Apple app stores, but additional mechanisms were put in place that made those apps non-functional even when they were pre-installed (before the ban). For example, Indian users see a network connection error message when opening a popular TikTok app (Figure 1).
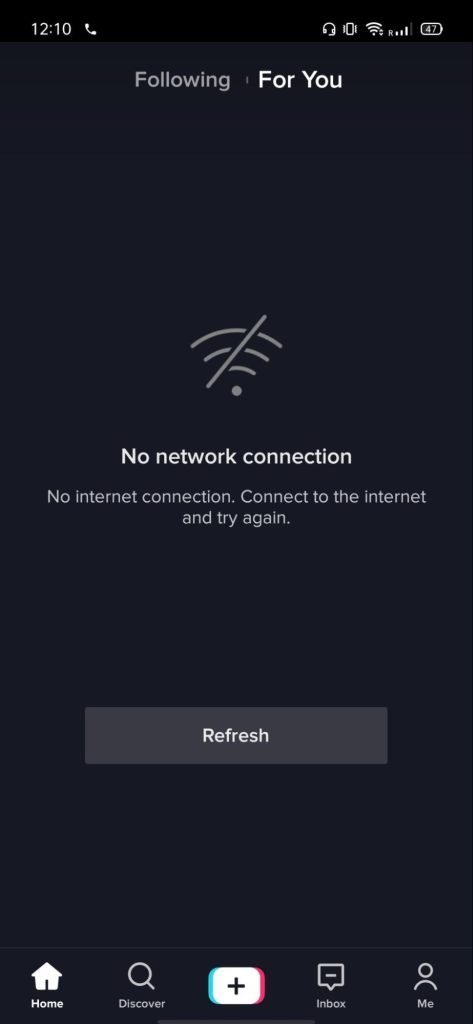
While web-based filtering has been extensively studied (see this paper and this paper), it was the first time such app-level blocking was observed, necessitating a thorough investigation of the employed techniques.
In a joint study conducted at Max Planck Institute of Informatics, IIIT Delhi, and BITS Pilani Goa, researchers revealed that app blocking is not performed by the Indian Internet Service Providers (ISPs) but by the app servers. This new blocking strategy departs from the known model of traffic filtering: ISPs restrict access to websites by placing firewall rules within their networks, but they have no role in app blocking. Refer to the PAM 2024 paper for more details.
Mechanics of App Filtering
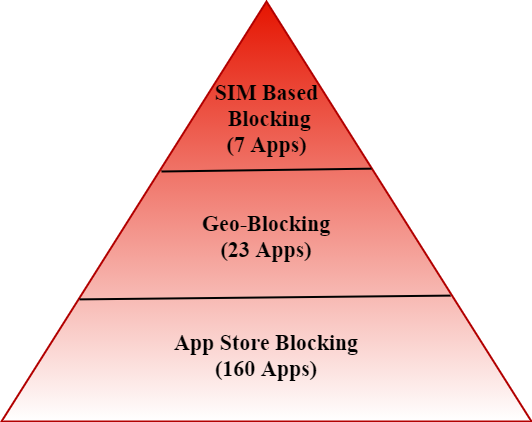
Researchers performed a thorough technical investigation involving reverse engineering some blocked apps. They used Man in The Middle Proxy (see link) to see the app’s traffic in plain text and inspected the code by decompiling the apps (see link). The analysis revealed three app-blocking tiers exist for Indian app users.
- Tier three apps are those that are unavailable in the Indian app stores. The researchers reported 160 such apps; users can access 136 directly after installation, such as Dawn of Isles and Game of Sultans.
- Tier two apps, after installation, would still suffer blocking. These app publishers selectively filter Indian clients using geo-blocking, restricting app traffic originating from IP addresses belonging to Indian ISPs. Twenty-three (out of the previous 160) apps belong to this category (for example, PUBG, Baidu, ShareIt).
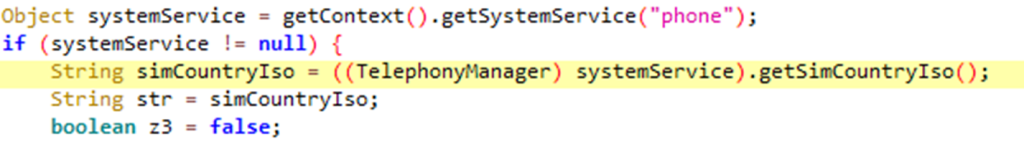
- Tier one apps employ the most sophisticated techniques. These apps block users by probing and extracting country codes from the SIM cards installed on their phones (see Figure 2). In total, 7 (out of the previous 23) apps employ such filtering techniques (for example, TikTok, UC Browser, V-Fly).
Bypassing the Server-side Filtering
To circumvent app blocking, the researchers obtained the .apk files of blocked apps from third-party sources (for example, apkmirror.com) and installed them.
After installation, most of these apps (136/160) were accessible and functioned as expected. The inaccessible apps belonged to tier two and tier one.
The tier two apps were accessible through VPNs, which changed the Indian source IP to a foreign one.
The remaining seven apps (in tier one) were accessible only when removing the SIM card and using a VPN. This step concealed the locale information from the SIM card and the IP address. Figure 3 summarizes the three blocking tiers.
Why App Publishers are Filtering Indian Users
It is natural to ask why app publishers are filtering Indian users when many of them do not operate from India.
Anecdotal evidence suggests that publishers hoped the ban would be temporary, and thus, they obliged. Some companies were communicating with the Indian government and awaiting their approval to relaunch the apps.
However, in January 2021, the government permanently banned all 220 apps. Even then, the app publishers continued the filtering and imposed stricter censorship for Indian users, while the ISPs had no role. The reason app publishers (and not ISPs) filter Indian users remains unclear.
The Road Ahead
Recently, the US House of Representatives voted to pass a bill that could lead to a nationwide ban on TikTok, citing the privacy concerns of American citizens. Following the existing app-banning model, many app publishers may adopt similar techniques stipulating the orders from competent authorities of different nation-states.
Alarmingly, apps can restrict users even without communicating with app servers. The logic to extract identifying users’ location (for example, from SIM cards) can be embedded within the apps’ binary. This is further cause for concern, and no doubt, more work needs to be done to investigate this area as more governments look to enact similar bans.
Ultimately, the risk of banning apps and services must be weighed with the impact of prohibiting people’s rights to information and the ability to access services via integrated login channels.
Devashish Gosain is an associated researcher at MPI-INF and an assistant professor at BITS Pilani Goa campus.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of the Internet Society.
Photo by Solen Feyissa on Unsplash

