Exposing the Roots of Phishing DNS Abuse
In short:
- Malicious domain registrations are concentrated, with attackers favoring specific registrar-TLD combinations based on pricing, bundled services, and operational policies rather than randomly registering domains.
- Domain registrars offering discounts and bundled services are more likely to attract malicious actors, while those enforcing stricter registration requirements tend to experience lower abuse rates.
- Proactive registration controls are effective, reducing abuse without deterring legitimate users.
The Domain Name System (DNS) is a foundational Internet protocol that, among other things, translates IP addresses to human-readable domain names. Unfortunately, cybercriminals also exploit it for a wide range of illicit activities, such as phishing, spam, botnet operations, and malware distribution.
Malicious domains eventually get blocklisted and suspended, forcing attackers to constantly purchase new ones to maintain their criminal activities. As previously shown, malicious registrations are not uniformly distributed—they tend to favor certain registrars and top-level domains (TLDs).
Recently, my colleagues and I examined more than 29,000 domains to identify the root causes of such abuse (see paper). We collected 73 features and categorized them into the following three groups that we hypothesize may influence attackers to favor a particular registrar-TLD combination:
- Registration attributes. These features outline the offerings available at the time of registration, including estimated retail pricing, discounts, accepted payment methods, and complimentary bundled services (e.g., free web hosting or TLS certificate).
- Proactive verifications. We verify if there are any measures in place to prevent phishing domain registrations, including contact information validation, keyword blocking, or registration restrictions (e.g., residence requirement).
- Reactive security practices. We send notifications to a subset of registrars and compare the malicious domain name uptimes to those we did not report on. Shorter uptimes should ideally discourage attackers from using certain TLDs and registrars, as swift suspension might drive them to seek alternatives.whether any measures are in place to prevent phishing domain registrations, including contact information validation, keyword blocking, or registration restrictions (e.g., a
Money Matters, But Not Alone
As part of our study, we built two statistical models to identify the driving factors of DNS abuse and compared malicious registrations to benign ones.
Our findings suggest that cybercriminals are price-sensitive, as a 1 USD decrease in the registration price is associated with a 6.6% increase in the number of malicious domains. Moreover, a one-dollar discount leads to a 49% increase in malicious domain registrations, highlighting a potential incentive for cybercriminals to exploit promotions.
Figures 1 and 2 below show the distribution of registration, renewal, and transfer prices for maliciously registered and benign domains, respectively.
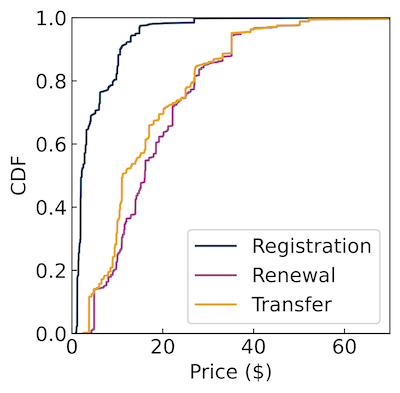
Registering a domain is typically cheaper than transferring or renewing it. Since malicious domains usually have short lifespans, attackers are less concerned with transfer or renewal costs. Registration prices of maliciously registered domains range from $0.78 to $69, with nearly 50% costing $2 or less.
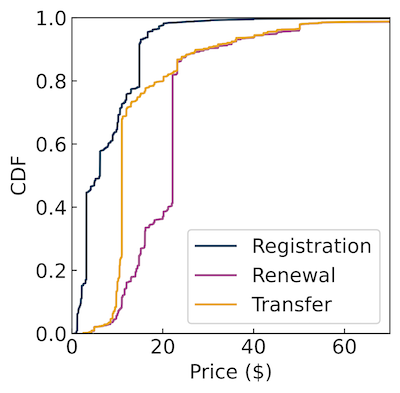
Conversely, the registration prices of benign domains tend to be higher, with a mean cost of $8.62 compared to $4.71 for malicious ones.
Free services also result in higher rates of malicious registrations. For example, free APIs are linked to a 401% increase in abuse counts. Such tools, when they provide API access for account creation and domain registration, may assist cybercriminals in quickly scaling up their malicious infrastructures. Free web hosting is also disproportionately favored by attackers, while free TLS certificates are attractive to both malicious and benign groups of users.
Proactive measures effectively decrease the abuse, as registration restrictions lead to a 63% decrease in the number of maliciously registered domains. Conversely, legitimate registrants do not seem to be deterred by such preventive practices.
Surprisingly, our results indicate that uptimes (i.e., faster mitigation times) have little effect on abuse counts. We hypothesize that even brief periods of operation can yield valuable credentials and financial rewards for attackers, limiting the effectiveness of reactive security measures focused on reducing uptimes.
No Single Feature is Determinative
Attackers are drawn to a combination of different factors that collectively increase the chances of abuse.
Operational characteristics such as unrestricted API access, aggressive discounting, and minimal identity verification highlight concrete intervention points. Still, any mitigation effort must be weighed against the complexity of implementation, operational cost, and the risk of deterring legitimate customers.
For more information, check our CCS’25 paper “Exposing the Roots of DNS Abuse: A Data-Driven Analysis of Key Factors Behind Phishing Domain Registrations”.
Yevheniya Nosyk is a cybersecurity researcher at KOR Labs, where she works on DNS, Internet measurements, and network security. She obtained a Ph.D in Computer Science from Université Grenoble Alpes in 2024.
Contributors: Maciej Korczyński, Carlos Gañán, Sourena Maroofi, Jan Bayer, Zul Odgerel, Samaneh Tajalizadehkhoob, Andrzej Duda.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of the Internet Society.

