Double-Edged Sword: How Attackers Use the Same Cloud Infrastructure We Rely On
In short
- Malicious actors are increasingly favoring partial use of cloud services rather than fully migrating their infrastructure.
- This diversity makes abuse harder to detect and mitigate.
- Security efforts should focus not only on fully cloud-hosted systems, but also on partial and mixed infrastructures.
Cloud computing is a foundational component of today’s Internet, enabling services to scale quickly and operate at low cost. These advantages have also made cloud platforms attractive to cybercriminals.
Recently, my colleagues and I used DNS data from OpenINTEL, cloud classification from IP2Location, and a curated ground-truth list of five market-leading cloud providers to investigate how attackers use cloud services and how this differs from typical usage patterns.
We examined three essential components of domain infrastructure, web hosting, DNS, and email, to understand not just where malicious content is hosted, but how attackers assemble their infrastructure.
Our findings suggest that cloud platforms are being used in increasingly selective and strategic ways, posing new challenges for Internet security and policy.
A Shift Toward Partial Cloud Usage
One of our key findings is that malicious actors are increasingly favoring partial use of cloud services rather than fully migrating their infrastructure.
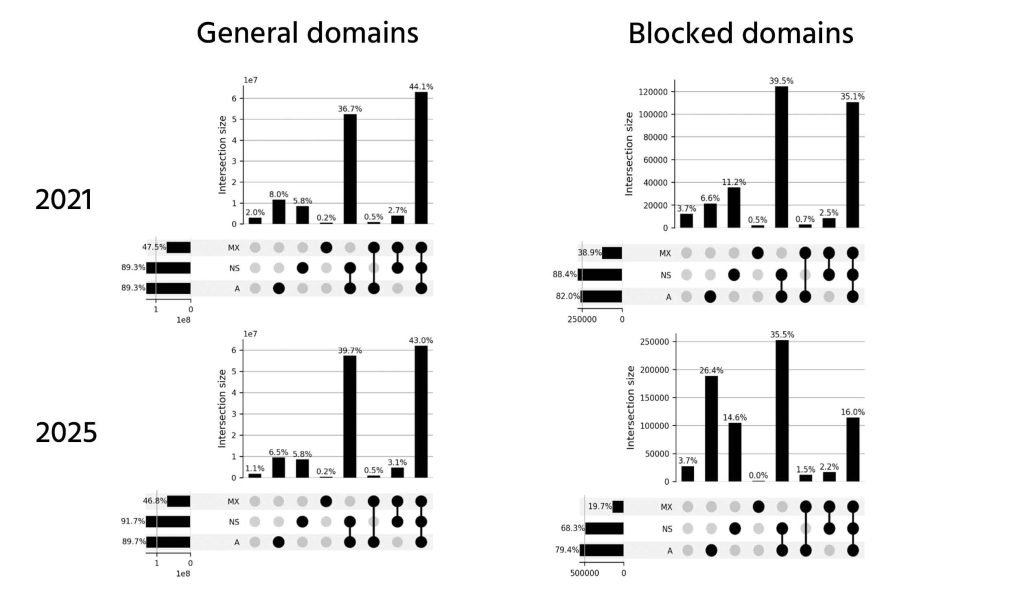
To understand how malicious infrastructure has shifted over time, we compared cloud usage patterns in 2021 and 2025 for both general and blocked domains. We focused on .com because it is the most widely used and an inexpensive top-level domain, making it common for both benign and malicious use.
Figure 1 shows that while overall cloud adoption across general domains has remained relatively stable, there is a shift toward partial cloud use rather than full-stack cloud deployment. This trend is particularly pronounced for blocked domains as attackers increasingly rely on cloud services mainly for web hosting. At the same time, the share of blocked domains using fully cloud-based infrastructure has dropped sharply, suggesting a growing preference for hybrid setups that may help evade detection or reduce dependence on a single provider.
No Single Cloud Provider Dominates Abuse
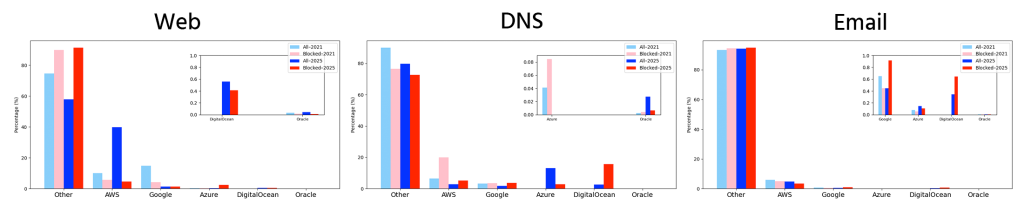
Despite major providers like AWS, Google, and Azure hosting many general domains, most malicious infrastructure is spread across a broader range of cloud providers. This diversity makes abuse harder to detect and mitigate, since there is no single point of control.
Importantly, having a large market share does not automatically mean hosting a large share of malicious domains. This suggests that provider policies, security practices, and abuse response mechanisms matter, even if their impact is difficult to measure directly.
Geography Still Matters
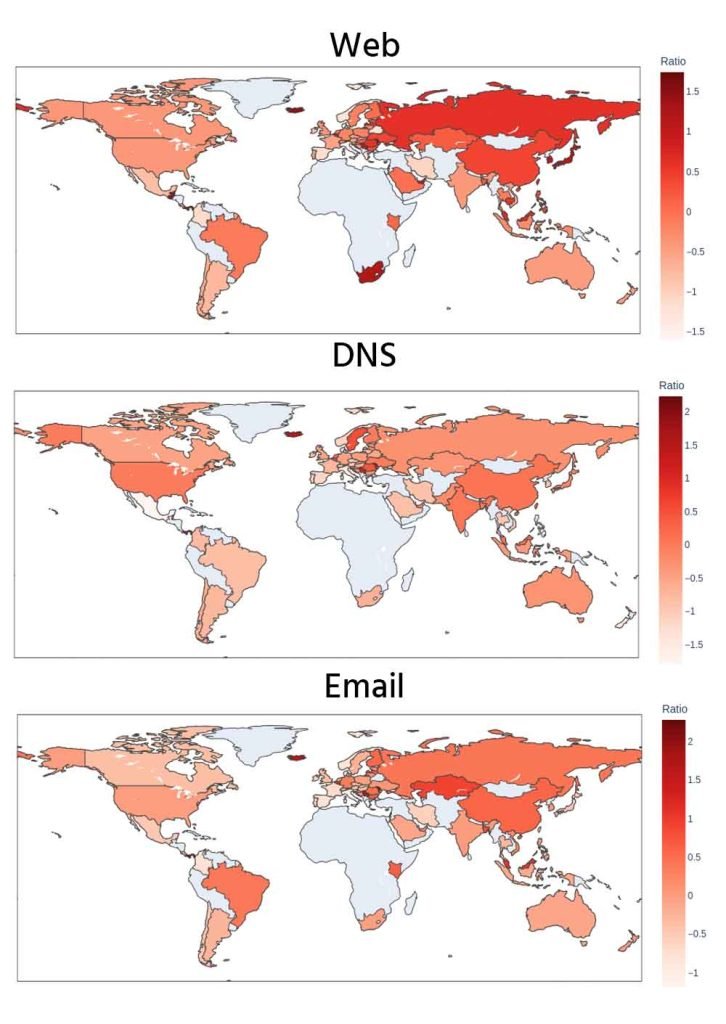
We also examined the likelihood that different countries host blocked domains compared with their hosting of general domains. Figure 3 illustrates where abuse is more prevalent than where many domains are hosted. Across web hosting, DNS, and email infrastructure, countries such as China and Russia show higher ratios of malicious activity, reflecting a higher relative concentration of abuse rather than absolute volume. Overall, the geographic patterns are consistent across infrastructure components, differing mainly in intensity.
What This Means for Policy and Practice
Our findings point to several important takeaways:
- Cloud abuse is evolving, and attackers are using hybrid cloud setups.
- Security efforts should focus not only on fully cloud-hosted systems, but also on partial and mixed infrastructures.
Cloud computing remains essential for an open and scalable Internet. However, as this research illustrates, protecting the Internet requires understanding how shared infrastructure can be misused and adapting defensive mechanisms accordingly.
Read our paper “Double-Edged Sword: An Empirical Study on the Contribution of Cloud Providers in Malicious Infrastructure” to learn more about our methodology and complete analysis.
Sousan Tarahomi is a PhD candidate in the Design and Analysis of Communication Systems (DACS) group at the University of Twente.

