DNS Hijacking in Malaysia: A Step Back for Internet Freedom
In short
- The Malaysian Communications and Multimedia Commission's attempt to implement widespread DNS hijacking has raised serious concerns about privacy, censorship in Malaysia.
- DNS hijacking occurs when ISPs or authorities redirect users' DNS queries to their own DNS server, allowing the to control what websites users can access.
- DNS hijacking is too broad and invasive a tool to be used without proper oversight, and it should not be relied upon as a means of content regulation.
In recent weeks, Malaysia has been at the center of a debate over Domain Name System (DNS) hijacking, which allows Internet Service Providers (ISPs) to intercept and reroute users' Internet traffic.
This attempt by the Malaysian Communications and Multimedia Commission (MCMC) to implement widespread DNS hijacking has raised serious concerns about privacy, censorship, and the future of Internet freedom in the country.
Although the government has since suspended these plans, the brief implementation revealed the potential for abuse and widespread disruption of Internet services.
What is DNS Hijacking?
DNS hijacking occurs when ISPs or authorities intercept users' DNS queries—requests to translate domain names into IP addresses. Instead of sending the queries to the user's chosen DNS service, such as Google DNS or Cloudflare, the ISP redirects them to its own DNS server. This allows the ISP to control what websites users can access, often blocking or rerouting traffic to restricted sites without the user's knowledge.
A related concept is the DNS Transparency Proxy, which intercepts DNS requests and reroutes them to specific DNS servers controlled by the network provider or the government—again, without the user's consent. This infrastructure manipulation is closely tied to Internet censorship because it allows authorities to prevent users from accessing certain domains or IP addresses. This method was used in Malaysia to block websites the government considered harmful, but the process affected many services.
In other countries like India, ISPs would implement DNS poisoning and injection techniques to achieve censorship. For instance, Indian ISPs might return an incorrect or blank IP address for certain politically sensitive websites, effectively blocking access without the user realizing it. This method is often used to censor topics that the government considers harmful or sensitive.
In Indonesia, similar methods have been used to block websites, especially those related to political dissent or inappropriate content. Indonesian ISPs intercept user queries and redirect them to a block page or return no result, making the content inaccessible.
[BREAKING NEWS]
— Frans Allen (@fransallen) April 17, 2022
You will no longer be able to use Cloudflare 1.1.1.1 or any other popular DNS resolver service in Indonesia.
ISPs have started blocking DNS services that can bypass censorship. pic.twitter.com/MSgtO0tDnR
While the technical methods may vary slightly between countries, the effects of government-mandated blocks are similar in disrupting users' ability to access information freely. These blocks, whether through DNS hijacking or other techniques, can cause widespread disruption to legitimate online services, as seen in cases where major platforms and services like YouTube and GitHub have been blocked in Indonesia and India.
Why is DNS Hijacking an Issue?
The use of DNS hijacking or DNS Transparency Proxies raises significant concerns due to the manipulation of core Internet infrastructure to address content problems.
The disruption of public DNS services like Google DNS (8.8.8.8) and Cloudflare (1.1.1.1) affected many legitimate services. Businesses, including hotels relying on reliable Wi-Fi services, experienced significant issues. Individuals taking online proctored exams also faced disruptions as these services were blocked or rerouted.
Moreover, these measures were implemented without sufficient consultation with the tech industry or public stakeholders. Poorly executed decisions without proper dialogue led to unintended consequences for various users and sectors. Furthermore, policies involving security-related traffic interception require adequate testing.
However, current tools like the Open Observatory of Network Interference(OONI) can only measure limited data on this issue, and some features remain in the experimental stage. The security risks remain significant when core Internet services are manipulated this way.
What Happened in Malaysia?
On 5 August 2024, the Sinar Project detected the use of DNS hijacking by Malaysian ISPs such as Maxis and TIME. Users accessing websites through public DNS services like Google or Cloudflare were unexpectedly redirected to ISP-controlled servers. These measures were implemented without public consultation, causing frustration and disruptions in access to Internet services.
TM started to hijack request over DoH (DNS over HTTPS), DoT (DNS over TLS), and hijack response. Malaysia great firewall! Have to option in for less common public DNS or use private DNS with unique personal url. pic.twitter.com/lkAGQ4qg3I
— Anaz Haidhar (@anazhd) September 5, 2024
By September, the situation escalated with some ISPs blocking DNS over HTTPS (DoH) and DNS over TLS (DoT), which are encrypted DNS protocols intended to protect users' privacy. The interception of DNS traffic on these ports (443 for DoH and 853 for DoT) further eroded privacy protections and user trust in online services.
While the government framed the move as a way to combat harmful content such as online scams and pornography, the blanket use of DNS hijacking raised concerns about political censorship and overreach. Speculation emerged that such measures could suppress access to politically sensitive websites, similar to past censorship during the 1MDB scandal. Following public backlash and concerns raised by civil society, the government suspended the implementation of DNS hijacking on 8 September 2024.
Why Was It Implemented?
The MCMC issued a general directive to block certain websites deemed harmful, such as those related to online scams, gambling, and pornography. However, the directive was implemented through blanket DNS traffic interception instead of a targeted and transparent approach.
ISPs were instructed to forward public DNS service requests to their DNS servers, effectively bypassing user preferences. As the policy evolved, ISPs like TIME began actively blocking external DNS services and requiring users to use only their own DNS servers.
The Immediate Impact on Services
DNS hijacking led to widespread reports of service disruptions, especially when it was implemented by TMNet, Malaysia's largest broadband provider. During this period, Artstation.com, a platform used by digital artists, was also added to the list of blocked sites. This was only confirmed through a government statement but on copyright grounds. As of 17 September, our report shows that Artstation remains blocked by current methods of DNS tampering by ISPs.
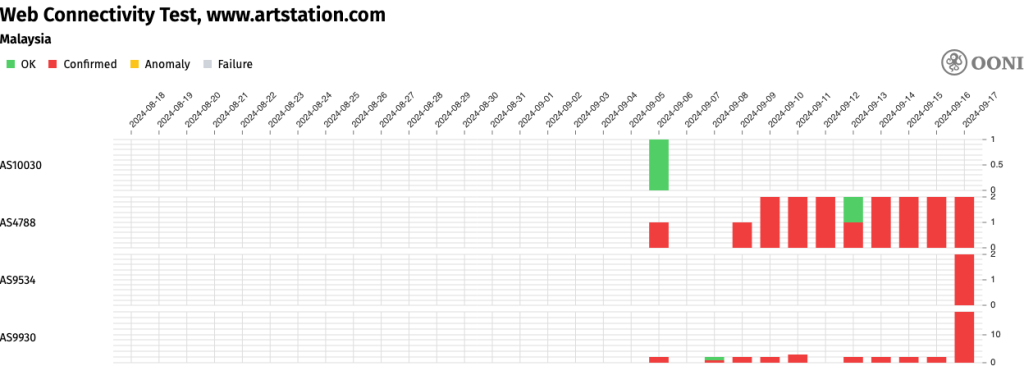
The blocking of trusted public DNS services, which many users and businesses rely on for speed and privacy, poses a significant threat to Malaysia's digital ecosystem. If these measures were fully enforced, Malaysia's reputation as a hub for digital innovation would suffer, potentially discouraging investment and damaging the country's digital economy.
What Needs to Change
While the MCMC has been instructed to retract its directive, the use of DNS hijacking reveals a dangerous precedent for Internet regulation in Malaysia.
Moving forward, any Internet regulation policy must be transparent and targeted. DNS hijacking is too broad and invasive a tool to be used without proper oversight, and it should not be relied upon as a means of content regulation.
Instead, the government or, in this case, MCMC, should:
- Be transparent about their Standard Operating Procedures (SOPs) for content blocking
- Publish a list of blocked websites by category with legitimate reasons
- Ensure that these measures are subject to public scrutiny.
Such policies should be developed through multistakeholder consultations involving civil society and technical experts to avoid overreach and ensure a balanced approach to content regulation. Without these safeguards, the public will continue to view these actions as efforts to suppress dissent rather than protect public safety.
Beyond immediate transparency, Malaysia's actions should be a wake-up call for the tech community to accelerate efforts in developing and implementing secure DNS protocols. Through working groups, the international tech community must prioritize DoH and DoT to prevent governments or ISPs from manipulating the Internet's core infrastructure.
For more information, check out the iMAP (Internet Monitoring Action Project) for Internet censorship updates and reports covering nine countries: Cambodia, Hong Kong (China), India, Indonesia, Malaysia, Myanmar, Philippines, Thailand, and Vietnam.
Numan Afifi is a Program Officer for the Internet Monitoring Action Project (iMAP).
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of the Internet Society.