Service blocking
Facebook, Twitter, Instagram
On 1st February 2021, the military in Myanmar carried out a coup d'etat, seizing power and detaining the country’s State Counsellor (equivalent to a prime minister) and other democratically elected leaders. There was an initial outage during the military takeover, followed by further mandated shutdowns and blockage. This blocking continues today.
Local impact
On 1st February 2021, the military in Myanmar carried out a coup d'etat, seizing power and detaining the country’s State Counsellor (equivalent to a prime minister) and other democratically elected leaders. There was an initial outage during the military takeover, followed by further mandated shutdowns and blockage. This blocking continues today.
Other supporting information
Starting from 4th February 2021 (3 days after the coup), OONI data shows that ISPs in Myanmar started blocking access to a number of websites – including Wikipedia, social media (such as Facebook, Instagram, and Twitter), and circumvention tool websites.
These blocks remain ongoing on some networks.
The following chart aggregates OONI measurement coverage from the testing of websites found blocked in Myanmar between February 2021 to April 2021 (excluding numerous other ongoing blocks which started before the coup).
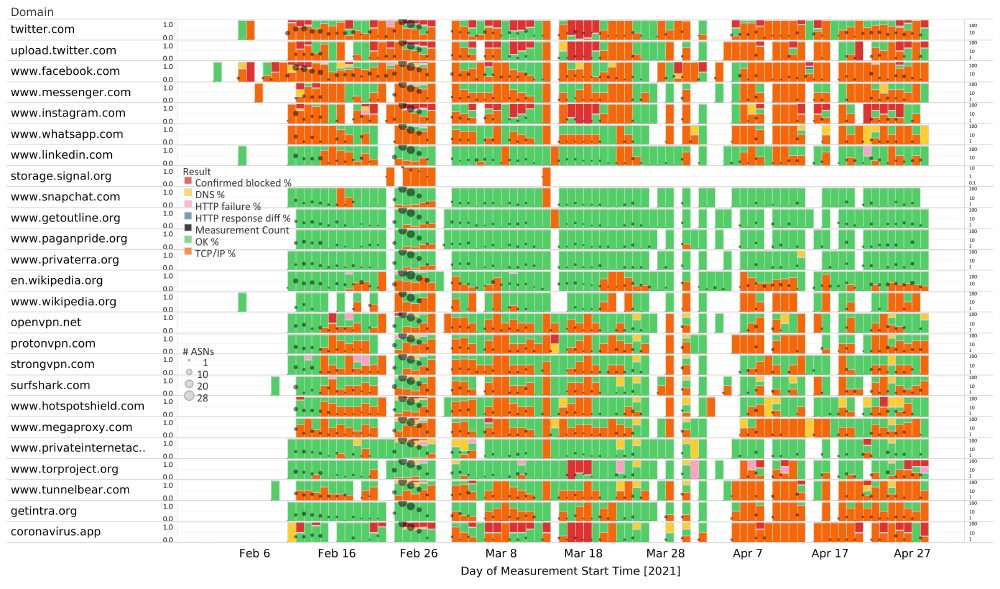
Source: Blocking of websites in Myanmar from February 2021 to April 2021 based on OONI measurements.
Based on the analysis of OONI data collected from Myanmar, OONI found:
- IP blocking became more prevalent after the coup. We primarily observed IP-based blocking of websites, as most OONI measurements (across ASes) show that TCP connections to the resolved IP addresses failed (when resolution succeeded in providing the right IP address for the website). This censorship technique is primarily seen in OONI data after the coup, as our analysis in Myanmar in 2020 showed that DNS based interference was previously more prevalent.
- Domains hosted on the IP 172.217.194.121. This IP address belongs to the Google hosting network and includes domains such as www.snapchat.com, www.getoutline.org, www.paganpride.org, and www.privaterra.org, all of which presented TCP/IP anomalies between 24th-27th February 2021 (as illustrated in the above chart). This suggests that some of these domains may have been blocked unintentionally as a result of collateral damage.
Overall, OONI found:
- Censorship variance across networks. We found different websites blocked on different networks, and different censorship methods used by different ISPs in Myanmar. This suggests that internet censorship in Myanmar is not centralized and that local ISPs may implement blocking at their own discretion.
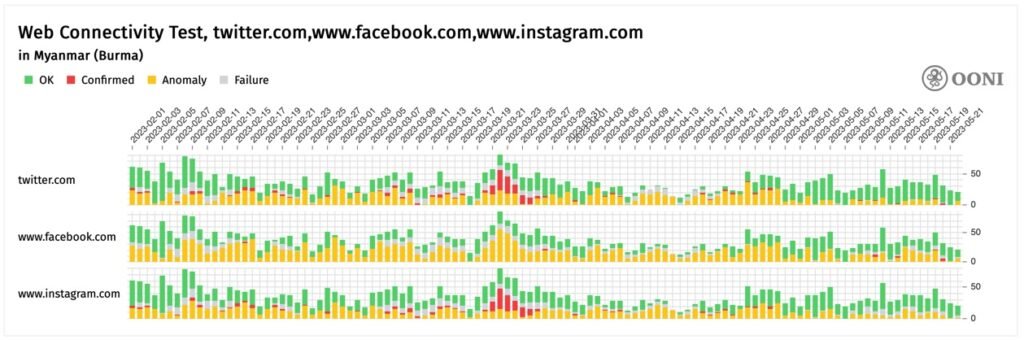
Over two years later the blocking of some sites continues, as shown in this chart from OONI:
May 2023 Update
October 2024 Update
As we are limiting our focus on service blocking, we are closing this incident page.
Social media
https://www.telenor.com/directive-to-block-social-media-service/ https://techcrunch.com/2021/02/05/myanmar-military-government-is-now-blocking-twitter/?guccounter=1&guce_referrer=aHR0cHM6Ly93d3cudGVjaG1lbWUuY29tLzIxMDIwNS9wMTY&guce_referrer_sig=AQAAAMYDPPlUEC8l812GvkDFxr8Y-UJpWY_Y1lRRd4Bj-eK9aBsE8ES59m2OWtw8mMRej9yFk4u8E9vZQkBZvesga6ESHPLVIfz3wWm3uCfHcIf6aAm6opBsfaxQNk_IYdmbnZoVK6O5J63BbQvn9zpZLlajYoQhOyCvJBQE8vpu_PEk

