A Decade-long Landscape of Advanced Persistent Threats
In short
- Between 2014 and 2023, 154 countries experienced an Advanced Persistent Threat (APT) attack.
- Government and defense agencies, along with corporations and businesses, consistently appeared among the top target sectors.
- APT activity often aligns with significant world events, including elections, international conflicts, and disasters.
Advanced Persistent Threats (APTs) represent one of the most sophisticated forms of cyber attacks today. Unlike ordinary hacking, APTs are long-term, highly targeted, and covert in nature. They are usually backed by nation-states or well-resourced groups pursuing political, military, or economic goals. Given the high severity of these attacks, numerous technical reports exist on the web.
Recently, my colleagues and I published a study at ACM CCS 2025, awarded the Distinguished Paper, that aimed to uncover this hidden landscape. We examined publicly available technical reports, documented threat actors, and security news articles, covering a decade of APT activity from 2014 to 2023. Our goal was to piece together how these campaigns evolved, what Cyber Threat Intelligence (CTI) patterns emerged, what common traits defined APT activity, and whether external events played a role in motivating these operations.
Evolution of APT Campaigns Over a Decade
Over the past decade, APT campaigns have impacted 154 countries, accounting for approximately 80% of the world (Figure 1). The United States (US), India (IN), and South Korea (KR) remain among the most frequently targeted.
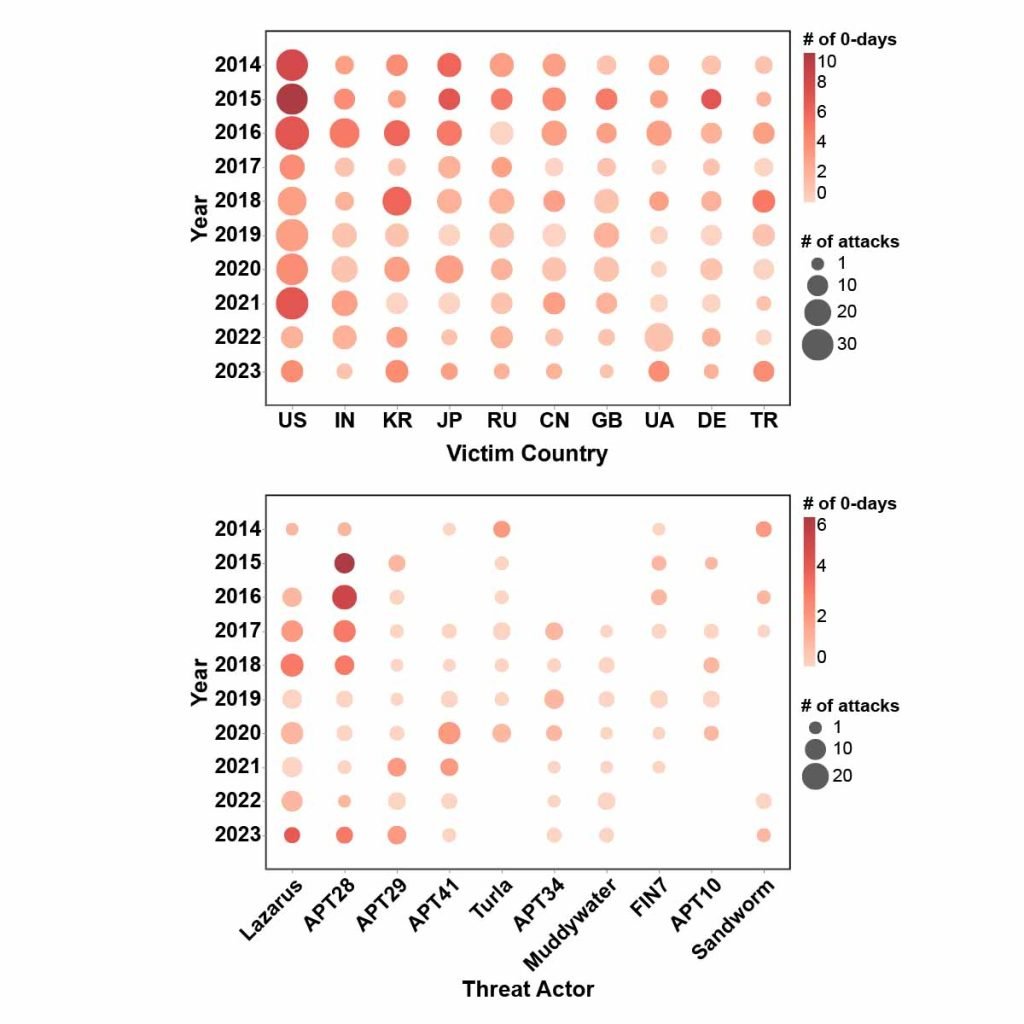
Despite the hundreds of groups named across different reports, only a handful, such as Lazarus, APT28, and APT29, are responsible for a significant portion of attacks. The number of zero-day attacks (# of 0-days) peaked between 2014 and 2016 before declining, suggesting that attackers increasingly turned to one-day (already-known, unpatched) vulnerabilities instead.
They also continued to rely on such attack vectors as malicious documents, spear-phishing, and vulnerability exploitation. Government and defense agencies, along with corporations and businesses, consistently appeared among the top target sectors.
Common Traits and External Dynamics
The CTI records we collated showed that attackers frequently employed tactics related to execution, defense evasion, and system discovery.
Windows platforms were frequently targeted, with remote code execution being the most common vulnerability type. One thing that stood out was how rarely malware detection rules were shared, likely due to confidentiality concerns, evasion risks, and the challenges of malware variability.
We also examined the duration of APT campaigns, which ranged from a single day to nearly five years, with operations lasting an average of 137 days. Approximately half were exploited as zero-day vulnerabilities, and half as one-day vulnerabilities, with an average patching time of 200 days.
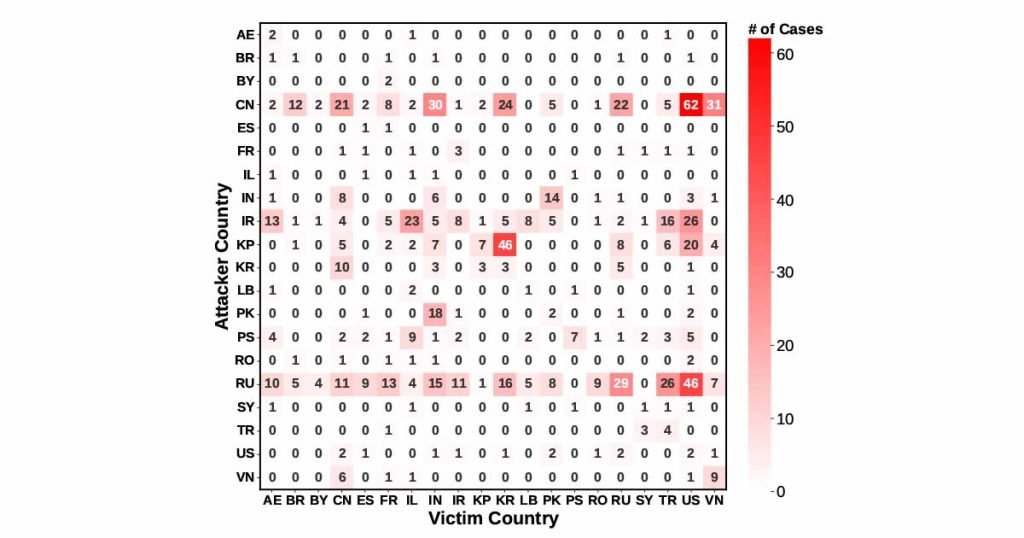
Figure 2 shows the APT activity across both attacking and victimized countries, revealing the attack asymmetries. For example, China launched 31 times more attacks on the United States than the other way around. Interestingly, some countries targeted their own domestic entities, often in the context of targeting individuals, political control, or surveilling foreign businesses.
We also found that APT activity often aligns with external factors, such as political events, international conflicts, global pandemics, and economic gains. APT groups exploit major political events, such as elections, with Fancy Bear targeting US and French presidential campaigns. Geopolitical conflicts often coincide with cyber operations, with Russian APTs launching attacks during international tensions. During the COVID-19 pandemic, healthcare and research organizations saw increased targeting from APT41, Lazarus, and APT29 groups. Economic motives also played a role: financially driven groups like FIN7 and Lazarus carried out attacks on banks and cryptocurrency platforms.
You can explore the visualizations and dive deeper into the APT activities through our interactive map and flow diagrams.
Shakhzod Yuldoshkhujaev is a master's student in the Department of Computer Science and Engineering at Sungkyunkwan University.
Contributors: Mijin Jeon (Sungkyunkwan University), Doowon Kim (University of Tennessee), Nick Nikiforakis (Stony Brook University), and Hyungjoon Koo (Sungkyunkwan University).
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of the Internet Society.

