Now There's a Way to Measure QUIC Targeting By Middleboxes
In short
- National-scale censors have been observed engaging in traffic filtering targeted at new and secure transport protocols such as QUIC.
- A new technique, IRBlock, developed under the Pulse Research Fellowship program, validates these claims and demonstrates its application in Iran.
- These results can inform policymakers and network protocol designers to increase the security and resilience of new transport protocols.
For more than forty years, the Internet has relied on the Transmission Control Protocol (TCP) to provide reliable transport between browsers and web servers. For most of this time, payloads sent over TCP were not encrypted, posing security and privacy concerns, particularly from middleboxes.
A middlebox is a device that can inspect and manipulate/block Internet traffic using pre-defined rules and heuristics. Many governments use them to censor content.
In the early 2010s, the adoption of HTTPS accelerated as individuals and organizations sought to establish encrypted channels over TCP connections. HTTPS, here, is short-hand for HTTP (the protocol used by web browsers), layered over an encrypted stream provided by Transport Layer Security (TLS).
However, middleboxes evolved to inspect destination server names (SNI) on outbound HTTPS connections, once again allowing certain authorities to block websites.
In 2021, the QUIC protocol was introduced as an alternative reliable transport for the web that overcomes these privacy challenges and is compatible with existing network infrastructure. QUIC is built on the User Datagram Protocol (UDP), over which it adds encryption and reliability. HTTP/3, the modern variant of HTTP built on top of QUIC, is now supported by all major browsers on both smartphones and computers. There is a high likelihood that this article was served over HTTP/3 to your browser.
Much like HTTPS, however, nation-scale censors have been observed to engage in traffic filtering targeted at QUIC. As part of my 2025 Pulse Research Fellowship, I sought to examine the application of packet analysis techniques of QUIC to validate these claims.
QUIC Censorship
Similar to HTTPS, a QUIC connection begins by sending the name of the destination server, among other parameters. This information is encrypted, but the encryption keys can be derived by packet sniffers on networks. So, what prevents a middlebox from applying the same connection interruption strategies as it did for TCP and HTTPS?
It's more difficult compared to TCP and HTTPS, but not impossible. First, a middlebox has to perform relatively more work to decrypt and inspect the QUIC handshake. Second, QUIC supports connection migration—a client that initially created a connection on a WiFi network would continue using the same connection after moving to a cellular network. This makes it difficult for middleboxes to track a connection across different modes of connectivity. But not impossible.
It’s Always the DNS
There's a protocol that's even more fundamental to the web—the Domain Name System (DNS). When a browser launches Google, it looks up the name google.com against a set of name servers. These name servers return the IP address of google.com, which the browser subsequently uses to make a connection over TCP or QUIC. If a middlebox can successfully disrupt DNS, it eliminates the need for more sophisticated disruption techniques targeted at QUIC. One such method of disrupting DNS is DNS Injection.
DNS Injection
DNS has been used successfully to disrupt connections to web servers at scale. This is because the most common form of DNS is not encrypted and, therefore, visible to middleboxes.
Disrupting DNS essentially prevents any subsequent connections to a website, regardless of the subsequent protocol.
A key method that middleboxes use to disrupt DNS is injecting incorrect responses to DNS queries. Figure 1 shows a browser receiving the incorrect response, 127.0.0.1, injected by the middlebox more quickly than the actual response, 1.2.3.4. The browser then attempts to establish a connection to 127.0.0.1, but this connection fails.
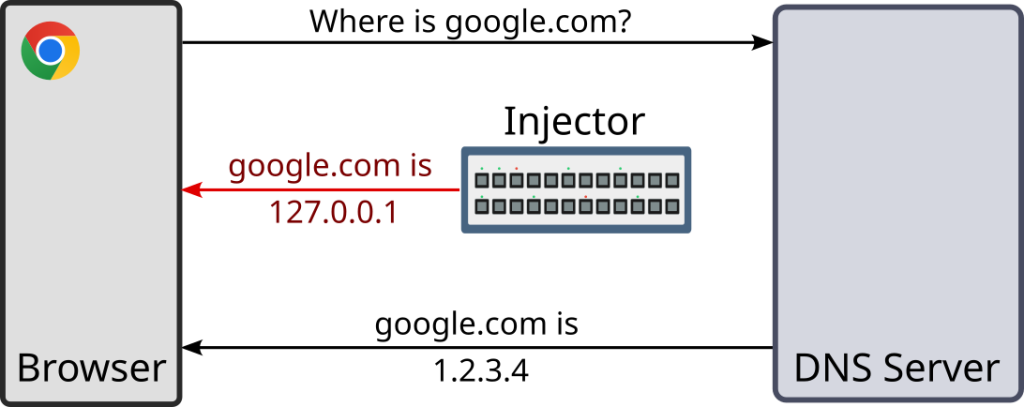
DNS injectors are often bidirectional — that is, they do not distinguish DNS queries originating outside their network from those originating inside the network. This enables researchers to study DNS injection in networks using measurement machines located afar. Because the machines performing measurements are no longer constrained to be inside specific networks, they can observe DNS injection at scale. When we sample network paths on the Internet using the presence of nameservers, we find a large proportion of geographies contain DNS servers that incorrectly return IPv4 addresses as responses for non-existent domains. These responses could be the result of a DNS injector or a misconfigured nameserver.
Inferring QUIC Interference
Our work relies on bidirectional injectors to infer middlebox behavior against modern User Datagram Protocol (UDP) payloads, such as QUIC. By analyzing the signatures of injected DNS responses, we predict censorship against UDP-based protocols, including those beyond DNS.
Our initial results strongly suggest the application of deep-packet inspection and filtering techniques on UDP using QUIC payloads in select autonomous systems in Iran.
Our results and technique (IRBlock) supplement existing research on QUIC censorship, with the added advantage of not requiring in-country vantage points or human volunteers to perform measurements. They also help inform policymakers and designers of network protocols about novel censorship strategies employed by large-scale networks worldwide.
For more information, refer to the paper 'IRBlock: A Large-Scale Measurement Study of the Great Firewall of Iran' that we presented at USENIX Security '25.
Karthik Nishanth is a Computer Science Master's Student at the University of British Columbia, advised by Prof. Nguyen Phong Hoang and Prof. Alexander Gamero-Garrido, and a 2025 Pulse Research Fellow.
The opinions expressed by the author do not necessarily represent the views of their sponsors and affiliations.

